SOC Platform, Product Announcement
Hunters SOC Platform Is Now Available in Databricks Partner Connect
by Hunters
Jun 1, 2023A few weeks ago, we announced the integration of Hunters SOC Platform with the Databricks Lakehouse, allowing Databricks customers for the first time to stand up a security data lake for security operations (data ingestion, detection, investigation and response) in just a few clicks.
Today we’ve reached a new milestone in the integration between the two products as well as our partnership with Databricks, as Hunters SOC Platform is now available on Partner Connect, Databricks’ centralized portal to help you find and integrate data, analytics, and AI solutions with your Lakehouse.
What can Databricks customers do with Hunters SOC Platform?
Build a Security Data Lake
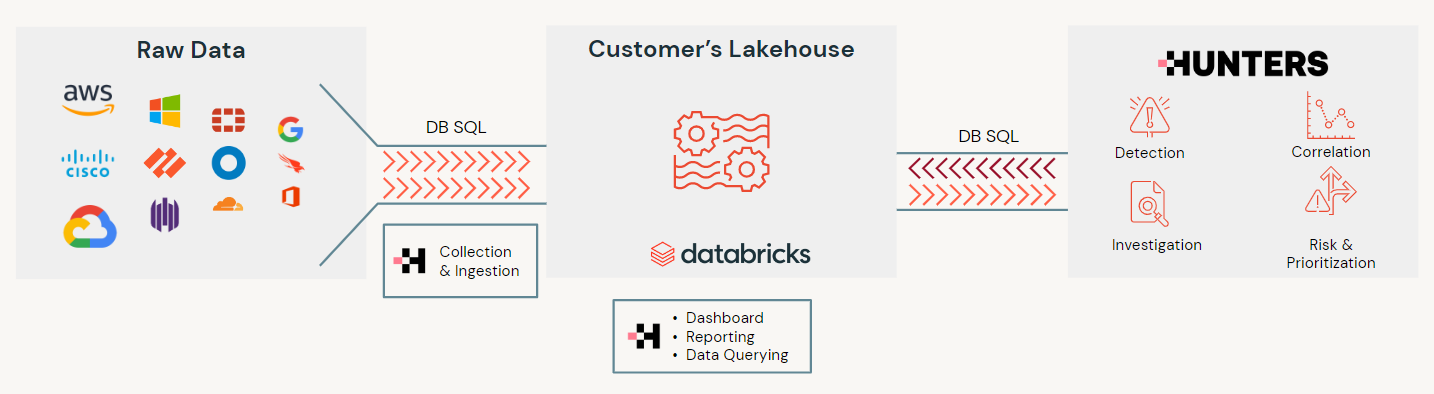
One of the biggest burdens of security teams today is managing the ingestion of terabytes of data from dozens of security products. Hunters eases this process with a state-of-the-art engine that provides scalable ingestion, monitoring and optimization. Moreover, it comes prebuilt with a large library of off-the-shelf integrations that can be set up in minutes.
Hunters SOC Platform ingests and performs the ETL of all security-related data into the customer's Databricks Lakehouse using the customer's cloud storage, so the customer gets to retain full ownership of all the security data. The Hunters ETL follows the Databricks' Medallion Architecture model storing the raw data and also normalizing the data into a unified schema that will facilitate further analysis.
Detect and Investigate Incidents
Hunters provides a library of hundreds of built-in detection rules that cover the majority of the threat landscape, mapped onto the MITRE ATT&CK framework. This allows customers to visualize coverage and understand their security gaps. All detection rules are pre-verified on real-world customer data to minimize false positives and excessive alerting. The detection rules are deployed directly to all customer tenants without requiring any action or tweaking, thereby automatically reducing the cybersecurity risk with little operational overhead.
Each alert also passes through an investigation engine, where it is automatically enriched with contextual information from various sources, and sophisticated dynamic scoring is applied to it to reduce alert fatigue and help security teams manage their SOC workloads more efficiently.
When the SOC analyst gets to an alert, all contextual information is provided in a single pane of glass to expedite triage and investigation. The contextual information goes beyond 'simple' enrichment of IP addresses with threat intelligence feeds, to deep correlation such as linking the user name in a CrowdStrike EDR alert with login records from the Okta authentication logs. Hunters' deep correlation capability is powered by a graph correlation engine: Alerts across entities and attack surfaces are automatically correlated on a graph.
Search & Incident Response
Having all of your security data stored in a modern data lake has great advantages for incident responders, and anyone who wants to gain insights on massive amounts of data.
Using Hunters and Databricks, customers can not only store petabytes of data, but also make use of them in their day-to-day investigations and in their most critical incidents. Some capabilities that support this are the following:
- IOC Search: Purpose-built search capability, allows responders to search all organizational data ingested by Hunters that resides on the Lakehouse for IOCs (IP, domain, hash) in seconds within the SOC Platform itself.
- Entity Search: Makes it easy to see all information about an entity in the environment in a centralized place. For example, from one suspicious login alert, customers can easily pivot to see the latest logins of the user in question across all endpoints, cloud infrastructure, and SaaS providers. In the same user interface, a responder can observe which alerts a user in question was involved in, and what is their role in the organization. Entity related views create huge efficiencies and productivity for security teams.
- Raw data access: all of your security data is available for you to dive into as you see fit, both from within the Hunters console, and from the Databricks interface. You can run queries on months of data, create operational dashboards that help expedite investigations, and run your own AI/ML models.
GETTING STARTED ON DATABRICKS PARTNER CONNECT
Simply search for ‘Hunters’ on Partner Connect.
Once you sign up, you’ll get access to a free version of Hunters, which allows you to:
- Easily connect and ingest your security data
- Quickly query and analyze data with built-in notebooks
- Take ownership of your data and access it anywhere
If you want to unlock the full SOC Platform experience, you can request access and one of our experts will guide you through.
* Note that Hunters SOC Platform is available for Databricks on AWS environments only.