Security Research, SOC Platform
Multi-Context UEBA: Evolving UEBA-Based Detection Capabilities
- By Hunters Research Team
- 6 minutes to read
TL;DR: Hunters has just released a new infrastructure that leverages advanced UEBA functionality across Hunters detectors. This infrastructure combats historic shortcomings of legacy UEBA solutions, by implementing dynamic thresholds, automatic tuning and cross-data source correlation.
User and Entity Behavior Analytics (UEBA) solutions promised to bring our security teams machine learning and automation that could detect every malicious event while ignoring everything that was benign.
Unfortunately, while UEBA functionality is a crucial piece of a complete security strategy, it has generally not lived up to that lofty expectation. If your team utilizes UEBA providers, you probably know the pains of the following:
- Dependency on static thresholds: different companies, environments, entities, or users all have different requirements when it comes to setting thresholds. An appropriate threshold for an entity in a small company, is most likely not the same threshold needed for a user at a large company. For example, if a UEBA provider writes a KQL query with a static threshold, it is highly unlikely that every organization will be able to use that query out of the box. It may fit some organizations, but others will have to spend resources tweaking the query or dealing with a mountain of false positives or a surplus of missed threats.
- Lack of automation: many UEBA solutions lean heavily on security teams for implementation and tuning. Teams must manually update the frequency at which their detectors run or adjust the mean and standard deviation to improve accuracy, relying heavily on humans to keep them both accurate and efficient. Without specific automations, this coverage feels more like ad hoc threat hunting rather than sophisticated behavioral analytics.
- Scalability: the effectiveness of UEBA can be directly correlated to how well the analytics scale across your environment. Most solutions are not capable of looking across multiple data sources (EDR, email, event logs, etc.) to correlate events appropriately, keeping the visibility limited to a subset of your environment. Additionally, traditional solutions rely on outdated data storage and compute structures, meaning that processing this large amount of data becomes extremely expensive.
- Poor signal to noise ratio: UEBA solutions constantly live in the balance between wide coverage and excessive noise. When a tool’s machine learning capabilities are limited and unsophisticated, high fidelity alerts become a luxury as opposed to the norm.
Introducing Multi-Context UEBA
At Hunters, we decided to approach these challenges head on and have built an infrastructure that brings new and improved UEBA capabilities to be applied across our built-in detectors.
Using Scala and Apache Flink as the groundwork, we are able to perform stateful computations over unbound data streams. We leverage Flink's state management abilities to constantly learn from the data, automatically reestablish our behavioral baselines and detect anomalies without needing to read the same logs twice. With this, we are able to create different UEBA detectors that reduce excessive alerting up to 90%. Yes, actually 90%.
This infrastructure can be applied at scale to add time series parameters to the backend of our existing and future detectors, making them dramatically more efficient than other solutions on the market. It is purpose built to enhance the detectors’ capabilities, but also to combat many of the common pain points surrounding traditional UEBA detectors.
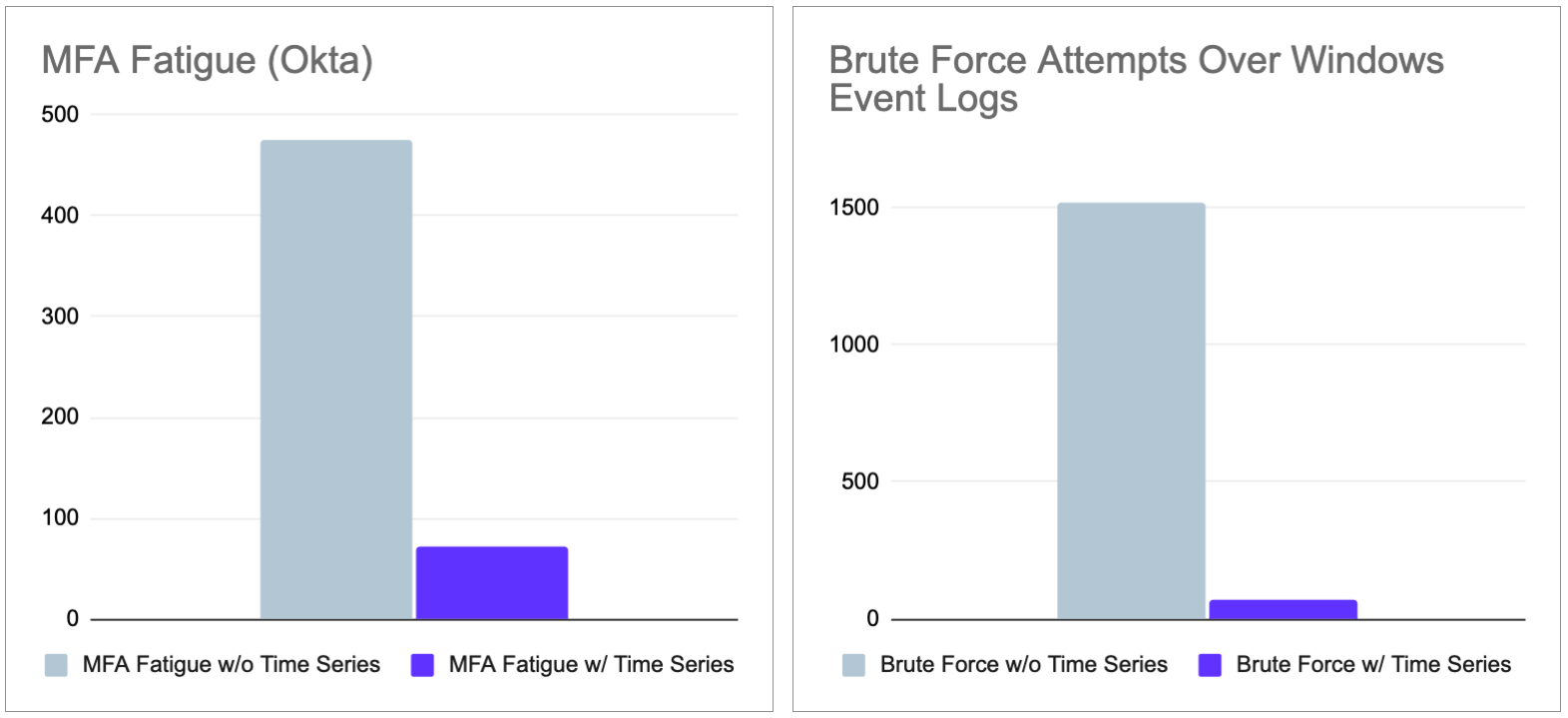 Implementing multi-context UEBA infrastructure to our existing detectors reduced excessive noise by magnitudes.
Implementing multi-context UEBA infrastructure to our existing detectors reduced excessive noise by magnitudes.
The time series infrastructure allows Hunters' detectors to combine the power of automation with dynamic thresholds, giving them the ability to adjust to specific parameters based on machine learning techniques.
This means that Hunters is able to watch and learn normal behaviors for specific users or entities across multiple data sources, so as not to flag them as malicious. To create the baselines for these multi-context detections, Hunters uses two kinds of time-sensitive checks:
- Skipping check: the Skipping check compares current behavior with past behavior in a corresponding time period (e.g., the same weekday and hour in the previous 8 weeks). Once an anomaly is identified, a lead is produced to notify that the system found an unexpected number of failed logins, compared to the expected calculated number based on past behavior.
- Continuous check: the Continuous check performs the same comparison, but its baseline is the recent past. For example, current behavior compared to behavior in the past 10 hours, hour-by-hour.
Hunters generates a lead whenever one of the detectors identifies a discrepancy between the expected behavior and the current behavior. Each detector is configured with a specific standard deviation threshold, and once this threshold is exceeded, a lead is created.
Configuring time sensitive checks like these requires focused expertise. Our Research Team has spent significant resources on developing and testing robust mechanisms that are both effective and reliable. Employing these mechanisms is what allows Hunters to offer a substantial upgrade from industry norms that employ static thresholds which either miss identifying anomalies or create an overwhelming amount of false positives.
Utilizing Hunters’ data correlation techniques, our UEBA detectors can identify anomalies across various contexts and time windows. With our big data processing engine, Hunters is able to process massive amounts of data across our customers’ vast security and IT stacks in near real-time, ensuring that every alert that is surfaced is enriched with all relevant contextual evidence.
Example: Kerberoasting Detector
To illustrate how this works, let’s use the example of Kerberoasting, a well known attack that can be really hard to detect.
During Kerberoasting attacks, attackers commonly will request an excessive amount from a TGS with weak encryption (RC4 or DES) in order to increase the chances of successful ticket cracking.
In our Kerberoasting detector, we use multi-context learning where we create baselines based on the username as well as the IP address from which the user requested the tickets. That way, if the user is compromised, the detector will notice that the tickets were requested from two IP addresses - one for the attacker and one for the user's legitimate IP address. Without using the context of multiple parameters, this detector would not be nearly as effective at correctly identifying malicious activity.
Once the activity is detected and a lead is created, Hunters also allows you to look deeper, by displaying the details of the data analyzed in order to create the lead.
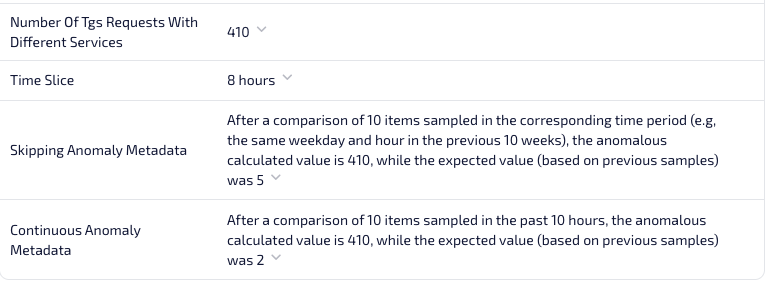 An example of the details shown in the lead summary. Here you can get a full explanation of why this lead was created according to both the skipping check and the continuous check.
An example of the details shown in the lead summary. Here you can get a full explanation of why this lead was created according to both the skipping check and the continuous check.
For example, in the case of the Kerberoasting detector, the lead details will show the number of TGS requests of different services performed by the same user and IP address. Unlike other industry offerings, this is not a black box of detectors that you must blindly trust. Here, you can truly understand what is the root cause of the lead and why it’s considered anomalous.
Hunters’ customers, like with the rest of the detection content, can benefit from these advanced UEBA capabilities from day 1, without requiring any tuning to work effectively. They are delivered built-in to the SOC Platform and are seamlessly updated without requiring any effort from our customers on their day to day.
UEBA is part of a complete security stack
It's important to note that UEBA detectors are just one component of a comprehensive cybersecurity strategy and are typically employed alongside other security measures. Adding this additional analytic capability to Hunters’ already expansive library of hundreds of pre-built detectors, means that your security team is continually improving their effectiveness by spending more time on the alerts that truly matter.
To learn more about Hunters' multi-context UEBA capabilities, book a demo here.


