Background: Too much data shouldn’t be a problem
Security operations today are dependent on technologies–predominantly SIEM–that too often hinder effective threat detection and investigation. Security operations have been conditioned to gather more data to improve visibility and accept the negative impacts of unmanageable financial and staffing costs because SIEMs can’t properly handle the scale and variety of that data.
This is where Hunters SOC Platform is breaking the pattern and instead effectively leverages more data to now drive down the noise and run automated investigations to derive clear, prioritized attack pictures for the analysts to act on. Hunters delivers this value from several capabilities, and one of them is IOC noise reduction.
Importance of IOC Feeds
IOC feeds are an important tool for security teams to stay ahead of emerging threats. They are lists of IOCs (indicators of compromise) like IP addresses, file hashes, URLs, etc. that a feed’s team has seen in an attack, via honeypots, or pulled from threat reports on the internet.
While these feeds are critical to many security teams, they are frequently noisy due to the imperfect means of collection. If a security team notices that an IP from an IOC list has appeared in their environment, it’s not clear whether they should pay attention or ignore it. Some IOC feeds are inherently noisy, for example flagging “malicious” files that are simply common and safe tools that were accidentally caught in the wide net cast by an IOC feed provider.
Hunters provides support for both free and paid IOC feeds in the platform, but unlike a SIEM, our research team actively improves our scoring models to reduce noise in these feeds.
Addressing the IOC feed noise problem
Hunters identified concerns about false positives generated by both the paid and free IOC feeds. Analyzing data on the leads generated by these IOC feeds, the Hunters research team determined the most common sources of noise for any feed, and identified improvements that could be made around consuming the IOC feeds.
Addressing the problem of IOC noise was well-suited to our research team and the Hunters platform because unlike other products, the automatic investigation capabilities in Hunters can prune IOC leads before they ever reach our users. So we focused on improvements to IP address and file hash IOCs.
IP address improvements
IPs are an inherently noisy IOC which presents challenges when determining false positives/false negatives. While we have built intelligent scoring models to evaluate IOCs, we originally had the same model for both outbound and inbound traffic that interacted with an IP address seen on an IOC feed. Our research showed that outbound traffic to an IOC IP had a higher signal than generic untargeted inbound traffic, and we confirmed that introducing asymmetric models would contribute to significantly reduced noise while maintaining true positives. We further updated our risk score to address if traffic to an IP was actually blocked, in which case the severity score of that lead would now be decreased.
File hash improvements
A source of noise across all file hash IOC feeds is binaries from known distributors being flagged as malicious. For instance, Hunters leverages the NSRL (National Software Reference Library) database to filter out hash IOCs before they can even be assigned to an alert, thereby dramatically reducing alert and false positive volumes.
We have also built new models from file enrichment data in VirusTotal to filter file hashes based on behavioral signatures. VirusTotal will run files in a sandbox and tag suspicious behavior like self-deletion – we now incorporate those tags into our dynamic scoring model. VirusTotal will also run files against multiple antivirus programs and report results – we changed our scoring model to adjust lead confidence based on the output of this enrichment.
Finally, we updated our models to increase confidence for hashes in user-controlled directories like downloads folders or temp folders, because we determined that those locations are more likely locations for a true positive IOC than our current baseline would suggest. We increased scoring for these file locations, while maintaining scoring for non-user folders.
Customer Outcomes
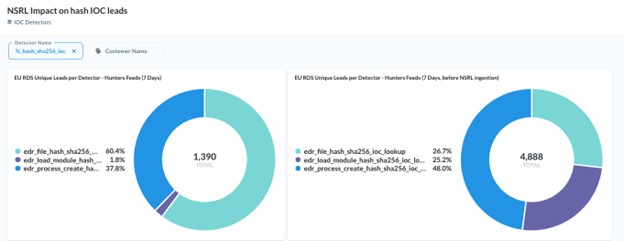
Hunters customers are now seeing a 66% reduction of file hash IOC false positives. Through IOC analysis from Hunters research it was clear that many were false positives in IOC feeds and were subsequently downgraded. For example, checking hash IOC leads for known distributors in the NSRL database alone contributes to reductions in leads per detector from 4,888 to 1,390.
Strengthening customer value with Hunters
Problematic SIEM tools are applying simple ‘if-then’ logic on an IOC list – and will just generate an alert if there’s a hit on an IOC list. The Hunters SOC Platform uniquely combines advanced scoring models to reduce false positive rates. While other platforms would require their users to build these models themselves or push this complexity to their analysts in the form of false positives, we have a sophisticated research team working full time on built-in detections, which includes IOC coverage. Furthermore, the Hunters Detection Engine supports scanning past data–so when a new IOC is published Hunters will automatically scan the customer’s environment for both new and past data and will alert if the particular IOC is seen.
While it’s great to allow users to write complex, custom rules, research projects like these IOC noise reduction improvements would require too much user investment. Instead, a multi-tenant SaaS platform like Hunters benefits from the collective metrics of our customer-based tune models, test hypotheses, and delivery improvements back to customers. And unlike SIEMs, these improvements are freely available and do not require any additional work by them.


