Detecting Ransomware: Putting Together the Pieces to Keep Your Organization Safe
- By Yonatan Khanashvili
- 5 minutes to read
TL;DR: Hunters has released a new set of security content into our SOC Platform that detects the most prevalent ransomware attacks, ensuring that our customers stay in front of the latest emerging trends in ransomware. See how Hunters builds an Attack Story to accurately identify a ransomware attack occurring across on-prem and cloud environments in this interactive tour.
Ransomware is a really big word.
It’s 2023, and yes, we are still talking about ransomware. Despite the increased media attention and industry awareness, there continues to be regular reports of ransomware attacks on organizations around the world, from large corporations to federal governments. The attack techniques are plentiful, diverse and always changing and threat actors are constantly refining their strategies, taking advantage of new technologies, and adapting their playbooks to maximize their profits.
These attacks can pose a serious risk to the stability of an organization, and for most, it is nearly impossible to keep up with new techniques that malicious actors are utilizing. At Hunters, we constantly strive to stay one step ahead, by researching the latest trends and building detections and playbooks to equip our customers with the tools to combat these types of attacks.
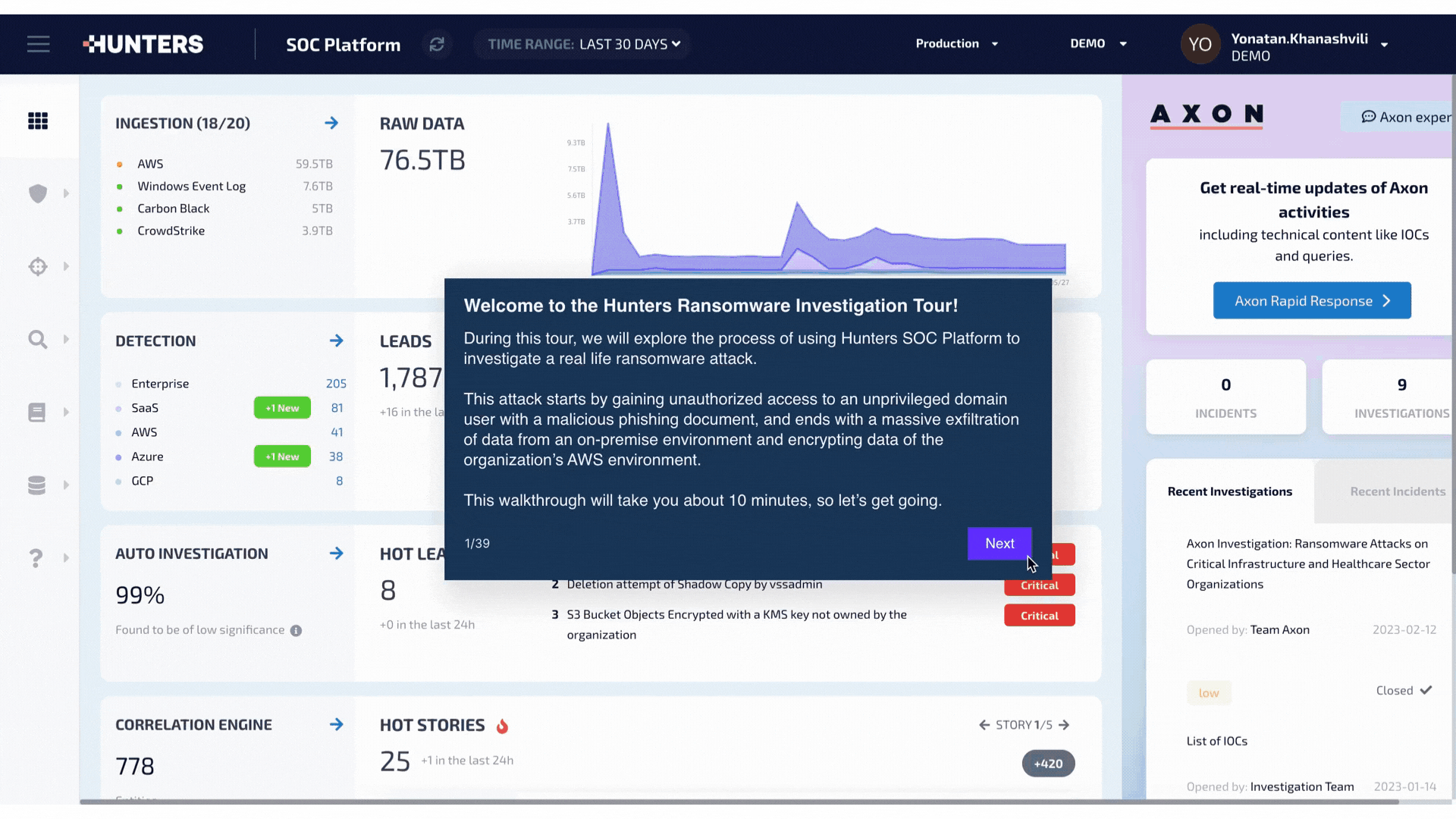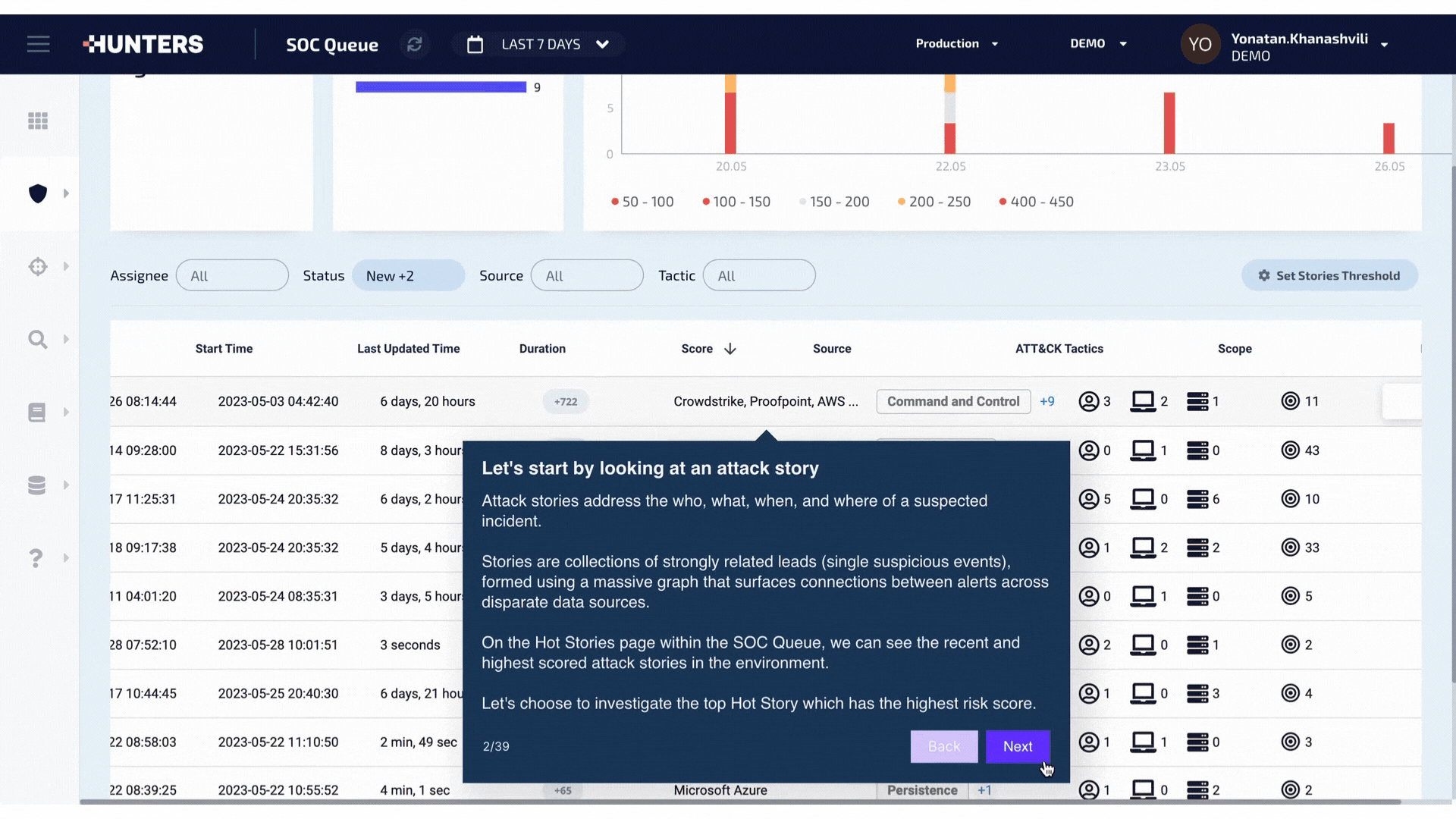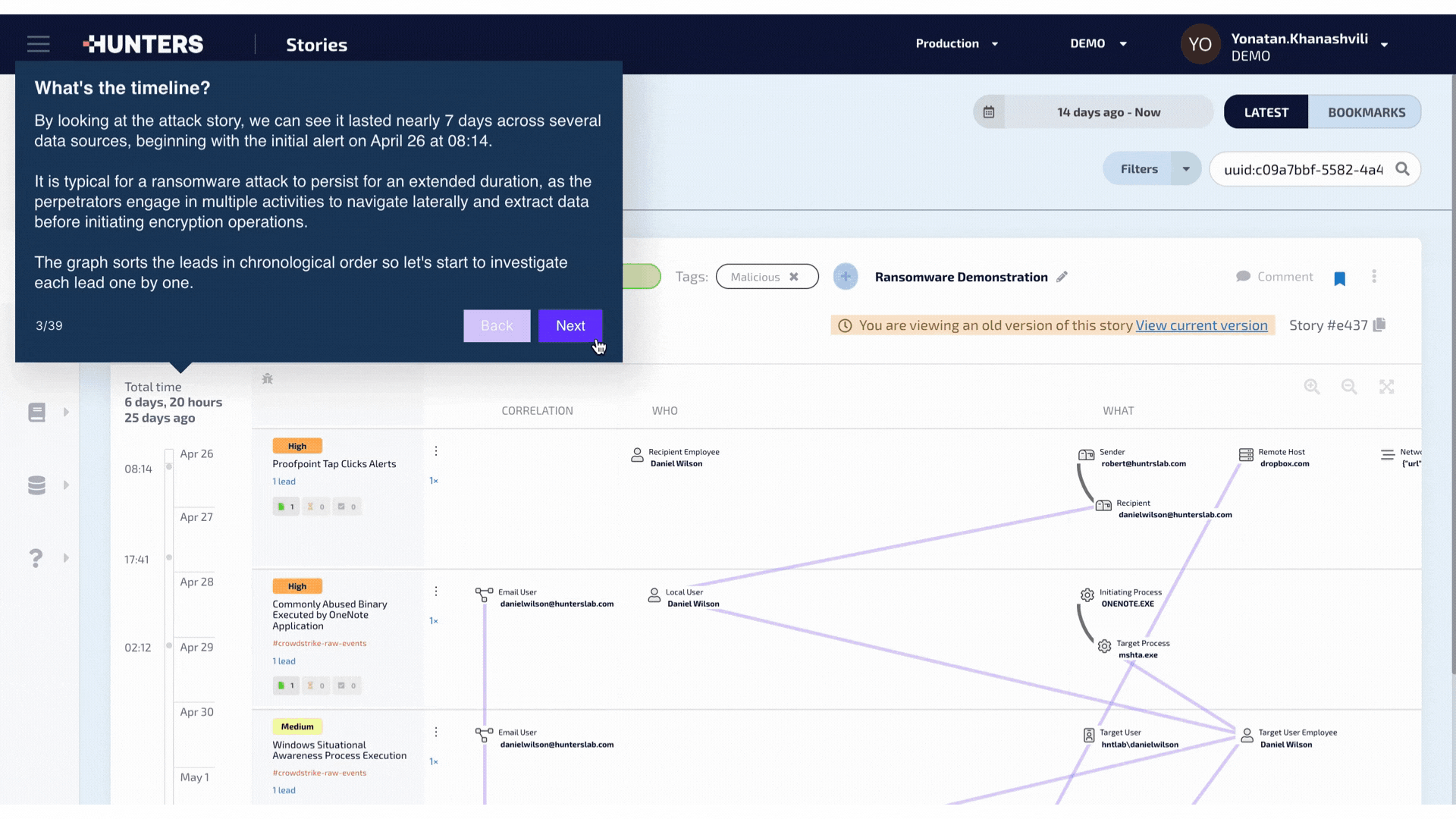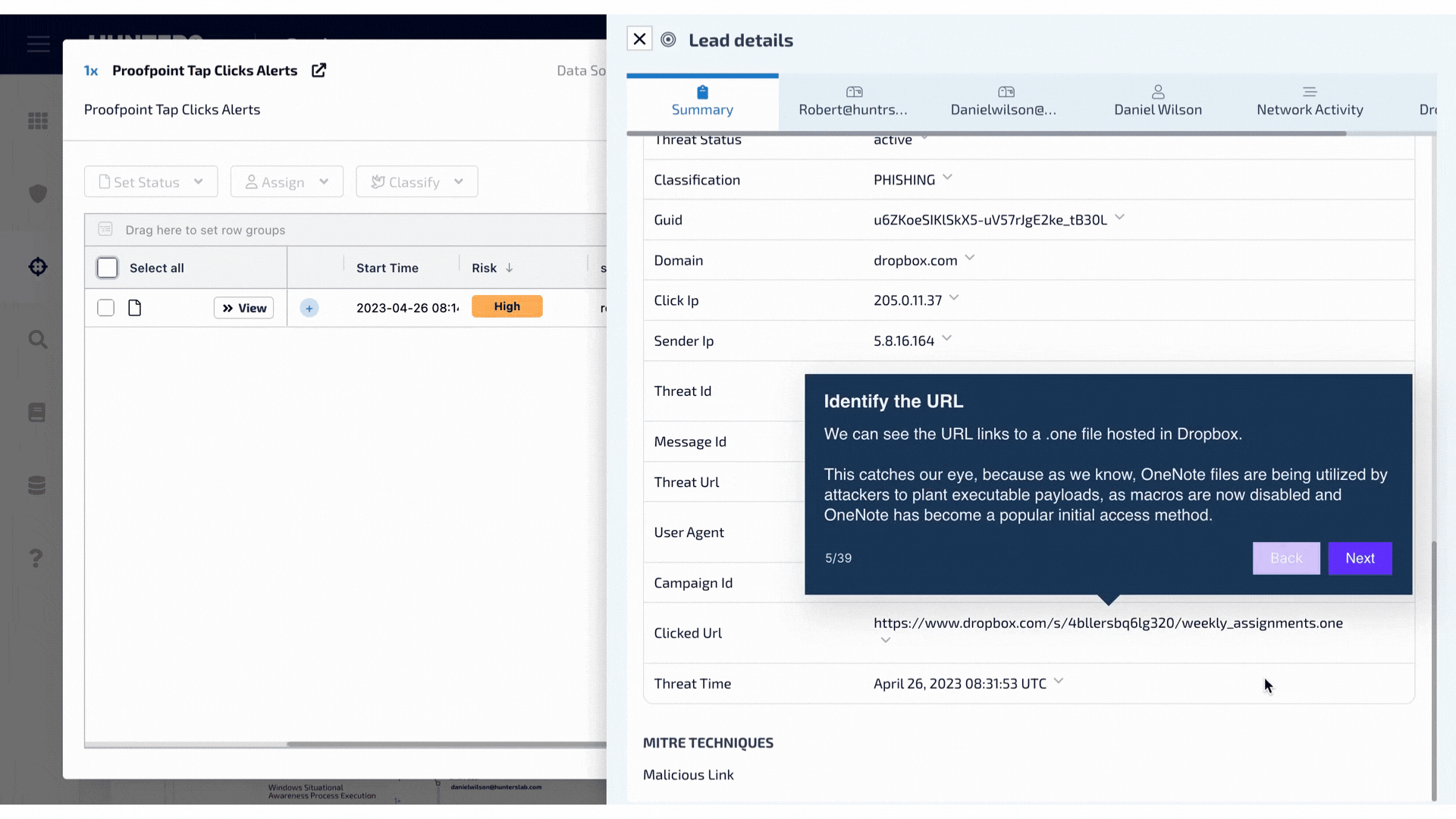
A look into the first few steps in the process of how Hunters helps you detect ransomware attacks across your entire environment. See the full walkthrough here.
Ransomware in the cloud
As organizations increasingly adopt cloud technologies to optimize business operations, this adoption also introduces inherent risks. Cloud attacks have become exceedingly prevalent, with threat actors leveraging misconfigurations, leaked IAM credentials, and vulnerabilities within cloud environments to compromise sensitive data stored in the cloud.
Recent high-profile breaches, such as the LastPass and Uber data breaches, have underscored the severe consequences of these attacks. Such incidents may not only result in unauthorized access to user data but also in potentially significant financial and reputational damage to affected organizations.
Given the increasing number of cloud-based attacks and the evolving tactics employed by threat actors (and with more and more organizations transitioning to storing their sensitive data in the Cloud), it is likely that we see a surge in cloud ransomware attacks.
Team Axon on the hunt
With this in mind, our team of expert full-time researchers embarked on an in-depth exploration of ransomware attacks both on-premises and in the cloud.
Evident in most ransomware attacks is not only the encryption of data, but also the exfiltration of it to an external location. Because of this, we extensively researched common exfiltration techniques employed by threat actors, including the prevalent use of Rclone, a tool favored by ransomware groups for exfiltrating and stealing data during security breaches.
Additionally, we delved into emerging and innovative methods witnessed in real-world scenarios, notably ransomware attacks that target data stored in Amazon S3. As one of the largest cloud vendors, Amazon S3 has become a target for many malicious actors, with the most common initial access vector being gaining access to IAM access keys.
The above are just 2 examples of ransomware TTPs our research touched on. We dedicated our time to creating detection logic to accurately combat these and several more, as well as performed proactive threat hunting campaigns on our customers’ environments to ensure that none had already fallen victim.
Detecting ransomware with Hunters
Going beyond theoretical analysis and ad hoc threat hunting we continued our research to test the efficacy of our new logic.
By replicating the attack in our lab environment, we were able to test our detection capabilities around the observed TTPs and ensure that combined with Hunters’ unique correlation capabilities, we effectively detected and alerted on the appropriate events.
This is where Hunters’ capabilities truly stand out - Hunters does the detection engineering work for you. By enabling our customers to detect ransomware attacks at the earliest stages across all of their security telemetry, security teams can view and investigate the entire attack via an Attack Story, showing all of the correlated events in a single pane of glass.
As ransomware exists across many attack vectors, it’s necessary to have a tool that can look across all of those vectors and correlate them to track lateral movement. For example, an EDR product will not be able to see events that come from email and email protection products can’t see what happens after that mail is delivered. When things are not connected within a single platform, the time to investigate these events skyrockets.
-3.png?quality=high&width=5569&height=2125&name=image%20(6)-3.png)
Correlation between shared entities across email and EDR data in Hunters
Hunters connects all of these events automatically and you can see exactly how this works when detecting ransomware in our walkthrough tour here.
The ransomware landscape is constantly changing, but it won’t be going away anytime soon. Hunters is here to help organizations of all kinds adapt to novel techniques by deploying new detection capabilities that drastically improve the time to detect and investigate these potentially catastrophic attacks.
-1.png)

