Security Research, SOC Platform
Asset Tagging: The alert prioritization method your security team needs to be using
- By Yonatan Khanashvili
- 6 minutes to read
In February 2020, threat actor groups targeting enterprises with Ryuk ransomware had collected over $61 million from their victims, delivering payloads in as little as 5 hours. Once in the network, the actors would use built-in Windows utilities such as Nltest to identify potential lateral movement paths in a technique called Domain Trust Discovery.
Nltest.exe is a native Microsoft command-line tool that is often used by system administrators to enumerate domain controllers, retrieve domain trust information, and to execute other administrative tasks. It can be abused by adversaries, as it was by Ryuk - but it’s typically used legitimately by sysadmins. This means that this is a low fidelity threat signal - one that could indicate an attack, but is much more likely to generate a false positive. So how can we tell if these low-fidelity alerts are real threats or false alarms? One powerful method is with asset tags.
What are asset tags?
Between servers, databases, and networking devices, enterprises have plenty of IT assets to protect, with varying levels of sensitivity. The most critical assets are the organization’s crown jewels - assets that, if compromised, can interrupt day-to-day operations, cause major financial loss, or leak sensitive data. These can include critical infrastructure servers, billing servers, and domain controllers. Since these assets are the most attractive targets for attackers, they need to be monitored closely.
Asset tags are ways to classify groups of related entities with shared characteristics and sensitivity levels in the organization. Some possible examples include:
- User identities, like “C-suite” or “Incident Response Team”
- User roles, like “Domain Admin” or “Cloud Service Account”
- IT assets like “Exchange Server” or “Domain Controller”
Why you should care about asset tags
Let’s go back to the earlier case of an attacker mapping an organization’s network using Nltest.exe. The following example is a threat signal detected by Hunters SOC Platform (hereafter referred to as a “lead”, Hunters’ term for threat signals).
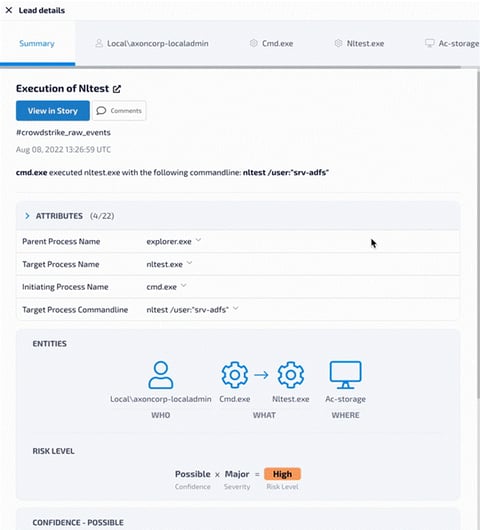
(Figure 1)
As you can see in Figure 1, this lead involves the execution of nltest.exe with the command line parameter /user:"srv-adfs", which returns information on the ADFS (Active Directory Federal Services) service account. ADFS is Microsoft’s identity access solution component, which allows domain users SSO access to services and applications both within the organization’s AD and in third-party applications. The command line you can see in Figure 1 was a part of enumeration activity, whose goal was compromising the ADFS service account, to access the ADFS certificate.
ADFS is responsible for authenticating users to approved applications by providing them with a signed SAML, that is then used to authenticate them to the desired application. Attackers can abuse this authentication process by stealing the ADFS Server certificate and using it to sign forged SAMLs with the stolen key, resulting in the attacker obtaining access to all services. This is called a Golden SAML attack and is notoriously difficult to detect by most security tools. For this reason, we consider the ADFS Server a sensitive asset.
In Figure 1, you can see that the lead has two asset tags - ADFS Server and Windows Server. The high sensitivity of the ADFS Server tag indicates that the behavior of this lead is highly suspicious and should be investigated to find out the whole chain of attack. Figure 1 shows the calculation of the lead’s risk level using the lead’s confidence level, or likelihood that the lead is malicious, and severity level, or potential impact of the security event on the organization. When a lead is tagged with a highly sensitive asset, its severity level is automatically raised, allowing for more effective prioritization of leads. Had this command been executed on a less sensitive asset, such as a user endpoint, the lead would be given a lower severity level and thus a lower priority.
The Hunters approach to asset tagging
In June 2022, Hunters introduced asset tagging to our threat investigation arsenal, as part of our Risk Score initiative designed to make alert prioritization faster and more intuitive in the platform.
Now that this feature exists, Hunters SOC Platform can automatically detect and classify the assets of an organization, providing out-of-the-box asset detection for asset types such as Domain Controller, Okta Admin, Exchange Server, Active Directory Certificate Services Server and many more. Each asset has a time-to-live, and is re-validated periodically to verify that the host or user is still relevant to the asset identified by Hunters. Assets are also each assigned a sensitivity level, which affects the tagged alert’s Risk Score calculated by our Automated Investigation Engine.
In addition to automatic asset tagging, security teams using Hunters can also manually insert custom assets into the product that are then utilized by Hunters’ Detection and Investigation engines to further aid in alert triage.
Conclusion
In this blog, we discussed the importance of making a distinction between a sensitive asset like ADFS and a less sensitive asset like a user endpoint. Using asset tags can make the difference between a high priority signal being investigated by an analyst or being lost in the noise. As in the Ryuk attacks, where a seemingly innocuous command was used for domain discovery, asset tagging may have been able to detect this sort of attack before the payload could be administered.
The various benefits to incorporating asset tagging into your security strategy include:
- Clarifying the asset type involved in an asset-specific investigation or hunting activity. This allows analysts to answer important questions such as:
- Is this asset vulnerable to this attack scenario?
- How severe is it if this TTP occurs on this asset?
- Were our Exchange Servers affected by this new CVE?
- Enriching security events with additional business context, which aids in the triage and investigation of leads, and the attack stories they’re involved in. This has the added bonus of helping new team members more easily get up to speed, or allow an MSSP to achieve a more complete understanding of the organization.
- Assisting in alert prioritization, by escalating low fidelity threat signals if they involve a sensitive asset in the organization.
To learn more about how Hunters can help protect your crown jewels, schedule a demo with one of our experts.