Advisory: Malware Targeting Organizations in Ukraine - Threat Hunting Queries
- By Team Axon
- 23 minutes to read
In recent weeks, several Russian-sponsored APT activities have been reported attacking Ukrainian organizations. These have been widely published in the security community. Hunters has been keeping on top of these reports as they come in.
While the threats continue to be tracked by Hunters’ Team Axon, we are releasing several hunting queries that can be used to hunt for anomalies that are related to specific behaviors associated with WhisperGate, HermeticWiper, and HermeticRansom malware.
This blog post focuses on threat hunting methodologies for malware-related TTPs that were observed during these attacks that will help you discover whether there is a malware-related activity in your environment, as well as technical details of these malware.
We highly recommend following the instructions in CISA’s advisory and hunting using the suggested queries below.
Malware Overview
Of the several different attacks, we will focus on three specific malware types: WhisperGate, HemeticWiper, and HermeticRansom.
WhisperGate Malware
WhisperGate targeted non-profit organizations and governments in Ukraine with what initially appeared to be ransomware but was quickly revealed as data corrupting software. As of the time of publication of this post, the wiper reported targeting Windows machines located solely in Ukrainian territory.
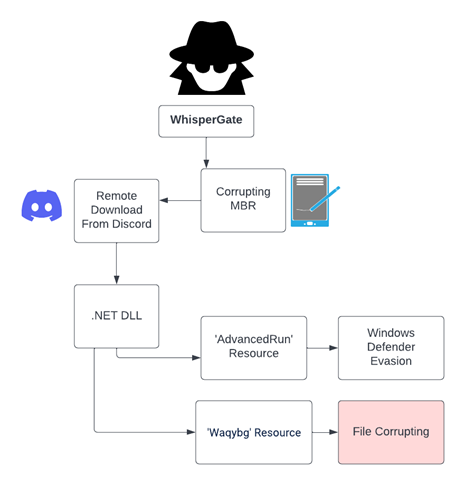
WhisperGate runs in a multistage approach, starting by corrupting the Master Boot Record (MBR) which will eventually prevent it from loading the operating system and displaying a fake message related to a ransom demand instead. The next stages include downloading the additional payload from the Discord External Attachment feature, and overwriting and destroying all the relevant data in the target machine.
HermeticWiper Malware
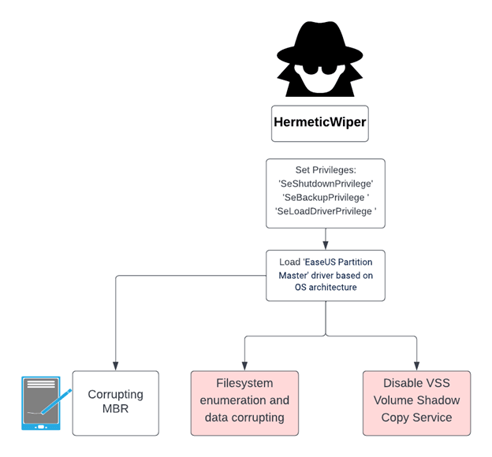
HermeticWiper is another type of wiper malware, aimed at slowing down the communications among the critical infrastructures in Ukraine by destroying files on infected Windows devices by corrupting specific elements of the connected harddisks. Unlike WhisperGate, which executed Win32 API calls, HermeticWiper abused a legitimate driver named EaseUS Partition Master in order to gain raw disk access and manipulate the target hard disk.
HermeticRansom (Partyticket) Malware
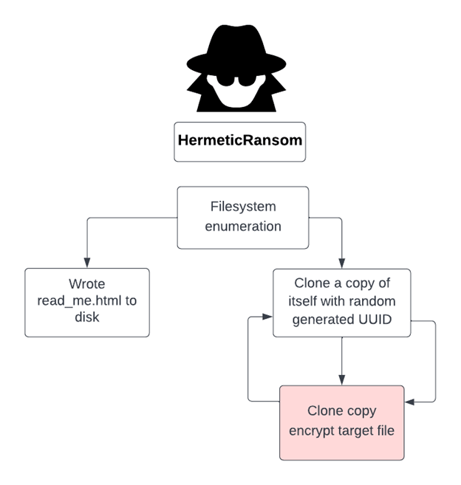
The Russian activity brought with it more attacks that aren't necessarily linked to the Russian government but have been seen targeting Ukraine assets during the conflict. ‘HermeticRansom’ (AKA Partyticket) appears to be one of them. PartyTicket is a ransomware written in Golang and aims to encrypt files on the target machine. The malware contains references to U.S. systems with strings, likely a political taunt.
PartyTicket was poorly written with an inefficient encryption process, and wrong initialization of the encryption key which results in the ability to decrypt the malware encrypted files, which again raises a question on who originally wrote it.
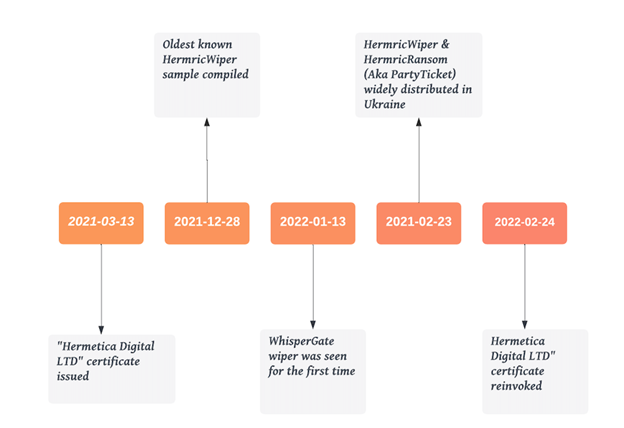
Below you can see the timeline of the malware used to attack Ukraine in the latest cyber attack.
Axon Threat Hunting Queries
Evasion - PowerShell Base64 Sleep Command
Upon communicating with a Discord server to download the 2nd stage, WhisperGate will sleep for a total of twenty seconds by executing a PowerShell command resulting in ten seconds' sleep, twice.
The following query looks for these encoded commands over Hunters' ‘EDR Process Creation Schema'. Hunters normalize process creation logs from various products and store them in the 'EDR_PROCESS_CREATION_EVENTS' table.
|
SELECT EVENT_TIME, |
Command and Control - Outbound Network Requests to Discord
WhisperGate uses the Discord external attachment service to download the malware's 2nd stage. Discord attachment service is known to be abused for malicious activity.
The following query aggregates processes that had network traffic to cdn.discordapp.com (which hosts Discord's attachment service) and provides statistics around them.
|
SELECT MAX(EVENT_TIME) EARLIEST_TIME, |
Wiper Activity - File Corruption
WhisperGate's main goal is to destroy and corrupt the files on the disk. It achieves that by overwriting the start of each targeted file with 1MB of static data.
Once the file was corrupted, the wiper will append a random four-byte extension to the file name. For example: file.9876
The following query aggregates a large amount of renaming operations with four-byte extension over one-hour interval over Hunters' EDR File Events Schema. Hunters normalize EDR file events such as rename, deletion, and creation from various EDR products to the 'EDR_FILE_EVENTS' table.
|
SELECT MAX(EVENT_TIME) EARLIEST, |
HermeticWiper
HermeticWiper Driver Installation.
HermeticWiper abuses legitimate driver of EaseUS Partition Master driver in order to gain direct raw disk access and to manipulate all relevant disks. The wiper stores four different driver architectures at one of its data sections and drops the relevant one, based on the target OS version and architecture, into system32\drivers directory named as 4 characters, randomly generated.
The following query will look for 4-character, randomly generated files with a ‘sys’ extension written to system32\drivers and has one of the 4 EaseUS driver versions' hashes.
|
-- HermeticWiper Driver Installation |
HermeticRansom
HermeticRansom performs an exclusive operation with its encryption process, which clones a unique executable for every encryption operation. The following query will look for HermeticRansom’s executable cloning process, which identifies multiple copy operations of randomly generated universally unique identifier (UUID) name binaries over a short time frame.
|
SELECT MAX(EVENT_TIME) EARLIEST, |
We hope you find these helpful. Subscribe to our blog to stay up-to-date with the latest research findings and rapid response campaigns by the Hunters team.
-1.png)

