To the Cloud and Beyond: Hunters is now Available on the AWS Marketplace
by Chris Sullivan, Head of Channels & Alliances and Yael Macias, Product Marketing Manager
Nov 10, 2021
Hunters SOC Platform is available on the AWS Marketplace. AWS Marketplace is a digital catalog with thousands of software listings from independent software vendors that makes it easy to find, test, and buy software that runs on Amazon Web Services (AWS). Hunters is available for AWS customers directly on the AWS Marketplace, simplifying the Hunters workflow and helping our joint Hunters-AWS customers solve the most important challenges faced today by security operations teams.
Using Hunters SOC platform, AWS users can address the criticality of data in threat detection and response on a scale that meets cloud expansion and exponentially growing volumes of logs. Data from AWS —such as CloudTrail, GuardDuty, Amazon VPC Flow Logs, and AWS WAF—gets intelligently processed and normalized into a single, unified schema to facilitate automated analysis across the entire security stack (cloud, endpoints, email, network and identity providers). The Hunters platform retains data in a “hot” manner, ensuring necessary coverage and rapid access for investigation and forensics, allowing for accelerating subsequent response measures.
Hunters SOC platform up-levels security analysts’ ability to see, understand, and respond to security incidents. We have packed expertise in threat hunting and attack techniques across AWS and other domains, combined them with threat intel, and built multiple layers of automation to present security analysts with a prioritized list of attack stories and their context, accelerating their understanding of what happened and how to address it. The result: a more efficient use of resources and more effective, faster and confident threat detection, investigation and response.
Key use cases that AWS customers can address by deploying Hunters into their security stack:
- Ingestion and normalization of telemetry at cloud-scale both from AWS as well as from multi-cloud environments that also use Microsoft Azure or Google Cloud Platform, and security data from the existing tools at the SOC. All of this data is intelligently processed in a cost-effective and predictable manner that fits modern security analytics requirements, incident investigation, and forensics needs.
- Unique automated detection capabilities that result from in-depth proprietary research from Hunters of AWS internals (i.e. knowledge of AWS's inner workings, in terms of how exactly logs are generated from each service and how each field is populated, how AWS temporary credentials are generated, etc.) These are presented in the Hunters SOC platform in the form of detectors that come out-of-the-box and generate alerts after passing a certain scoring threshold. Hunters also maps detections onto the MITRE ATT&CK framework so users can understand up front what they can and cannot detect with the data sources connected to the portal. AWS users that don’t have Amazon GuardDuty can still attain sophisticated threat detection coverage and monitoring with Hunters.
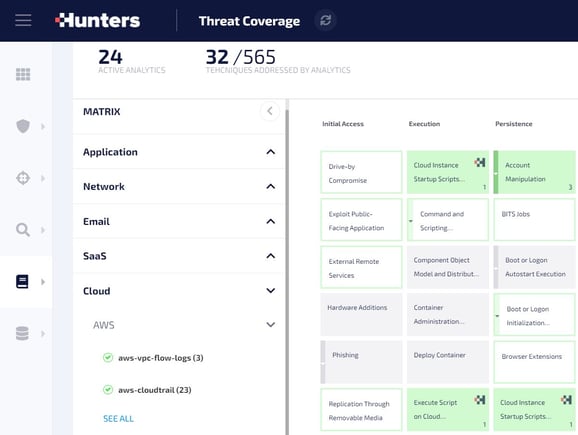
AWS data flows mapped onto the MITRE ATT&CK framework to show the current threat coverage of the organization
- Visibility into AWS users and/or systems across different platforms: Hunters correlates AWS-specific identities with users or email information from other platforms and data sources based on person-matching or other contextual information (i.e. who created this user, etc.)
- Investigation capabilities similar to Amazon Detective but more advanced and thorough since Hunters bundles them with the rest of the investigative capabilities of other domains to deliver better visibility into entire attack flows all in one platform.
- Connecting AWS session activities into single stories: Hunters gives a clear understanding of what a specific user or system has done in an AWS session accurately and in near real-time by tying different activity logs into a sole story.
Hunters' unique Person-matcher mechanism connecting an alert from Carbon Black Defense taking place in an endpoint with a log from Okta notifying of a failed MFA challenge
- Two-way insights and correlation between cloud and EDR: Hunters provides cloud-related context and correlations to threat signals and native alerts from EDRs running on a cloud instance and vice versa, receiving rich host-level context on cloud-related threat signals and native alerts from EC2 instances that have EDR agents installed from CrowdStrike, Carbon Black, SentinelOne, etc.
Ideal for security operations teams working to contain technology sprawl, adapt to cloud-scale, and extend the value of the existing data streams, Hunters has been adopted as a SIEM replacement by some of the world’s largest enterprises.
On behalf of the entire Hunters’ team, we are excited to continue building upon our relationship with Amazon Web Services by establishing our presence on the AWS Marketplace as a central tool for Security Operations.




